To Contact Hook Me Up Call
Contact us at the Consulting Hookmeup office
(205) 623-0745
Access Control System
Keep safe your home with authorized personal safe and secure access
Remote Management
Streamline Provisioning
Extend Your Security Standard to the Door
Meet Compliance Needs
By now, you’ve probably heard of access control and explored its benefits and applications in the modern office or facility. However, choosing to implement one can be quite a difficult decision, especially considering how many options there are when it comes to hardware, software, manufacturers, installers and management systems. It can be daunting even for the most seasoned security expert. That’s why it’s important to consider the impact of an access control system before going all in on one. The main considerations for a useful access control installation are both varied and incredibly important, so read on to find out how to get started.
OBJECTIVES
The purpose installing your access control system should be clear from the get-go based on the security level that you require for your facility. For instance, high-value assets like servers, communication equipment and mission critical data should be safeguarded at every access point to keep it safe from harm, while amenities like bathrooms and vending machines can have security that is a little less robust. Consider the sensitivity of the assets within your facility and plan to protect them accordingly. Protected behind a locked door, they become much harder to steal or compromise.
There are many different types of access control systems, which can make the selection process somewhat difficult. You don’t need to know all of the ins and outs of every method, but you should narrow it down to your top one or two types. For example, systems can be standalone, integrated, mobile-based or cloud-based, plus any other customized solution that you might want to explore. Cloud-based systems are becoming the gold standard of access control, so you might want to choose a system that features this integration
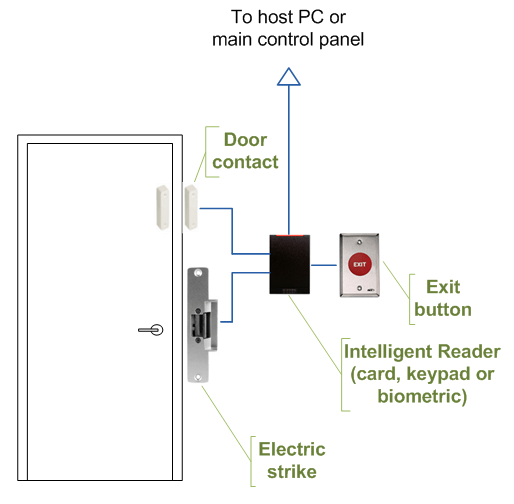
HOW TO INSTALL ACCESS CONTROL SYSTEMS?
A typical process should be based upon pre-assessed and pre-planned methodology, which may go as given below:
- Unpack the required access control system equipment and accessories
- Install pathways, ducts, closets and terminals of cabling
- Lay the cables, if wired technology is used otherwise install the wireless routers at the designated points
- Install door locks and door readers at every door
- Install sensors at the planned points
- Install main controller at the central point and connect through wires or wirelessly
- Connect the power cables, if not using PoE system
- Hand over the installation to the configuration engineer after physical power on testing
Disclaimer: State of Alabama Notice. If Customer is a resident of the State of Alabama, complaints may be directed to: The Executive Director, The Alabama Electronic Security Board of Licensure, 7956 Vaughn Road, Suite 392, Montgomery, AL 36116. Customer may also call (334) 264-9388 or fax to (334) 264-9332. License Number AL 060
